Intro
Using static and long-term credentials like IAM Access Key for AWS or Service Account Key for GCP could be easier to setup. However, once those credentials are leaked, unauthorized parties can get access to your resources and the revocation would be strenuous.
Therefore, the usage of short-lived dynamic credentials is urged. Since there is no static value to be stored/distributed, the related information would be harder to be leaked. This would also come with attribute based mapping and filtering that facilitate to the more granular access control.
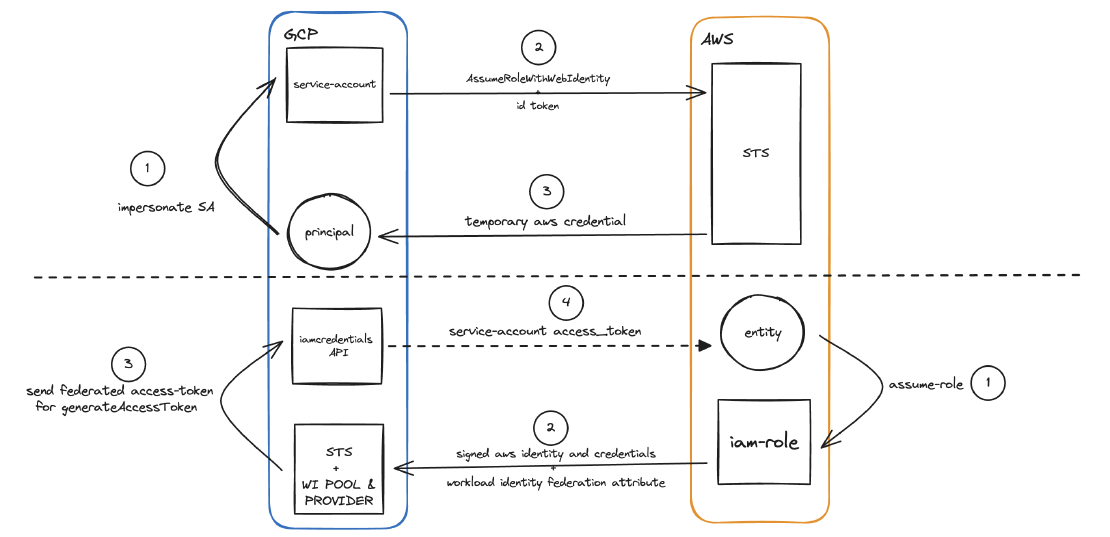
In this example, I would like to cover the usage of AssumeRoleWithWebIdentity and WI Federation between AWS and GCP to avoid having hardcoded credentials shared amongst each resources.
Prerequisites
You need to have following tools installed before proceed:
- gcloud CLI
- AWS CLI
- Python3. Ensure to also enable pip, pipenv, and virtualenv
- Terraform
In my case, all of those tools were installed and managed by asdf except terraform which is managed by tfenv .
Materials
All sample codes and scripts are stored in this repository - https://github.com/franzramadhan/franzramadhan-dot-dev-materials/tree/master/02-gcp-to-aws-short-lived-credential .
Check and adjust accordingly based on your need. If you think my example aligns with what you need, you can simply check the README and set the mandatory files and variables.
Authenticate to AWS from GCP using AssumeRoleWithWebIdentity
“AssumeRoleWithWebIdentity returns a set of temporary security credentials for users who have been authenticated in a mobile or web application with a web identity provider. Example providers include the OAuth 2.0 providers Login with Amazon and Facebook, or any OpenID Connect-compatible identity provider such as Google or Amazon Cognito federated identities.”
In order to enable AssumeRoleWithWebIdentity, we need to obtain service account credentials on Google Cloud and exchange it to the AWS role credentials.
Action Items
Create a service account in GCP
Get and note the service account unique id
Create IAM role in AWS
In the assume_role_policy, set to allow federated access from google account as well as service account unique id only. Something like this:
{ "Version": "2012-10-17", "Statement": [ { "Effect": "Allow", "Principal": { "Federated": "accounts.google.com" }, "Action": "sts:AssumeRoleWithWebIdentity", "Condition": { "StringEquals": { "accounts.google.com:aud": "<service-account-unique-id>>" } } } ] }Once it’s completed. You can get the credential by sourcing from our script as the external process. See source credentials with an external process .
AssumeRoleWithWebIdentity Material Resources
You can get a quick overview of the steps above by looking into these resources:
- Terraform Code for Provisioning the GCP service-acccount
- Terraform Code for Provisioning the AWS IAM Role
- AssumeRoleWithWebIdentity Technical Implementation
- Script to Assume AWS IAM Role from GCP SA
Workload Identity Federation from AWS to GCP
Using workload identity federation, workloads that run on AWS and Azure can exchange their environment-specific credentials for short-lived Google Cloud Security Token Service tokens.
For the complete picture and setup, you can look from this official GCP Documentation for Configure workload identity federation with AWS or Azure .
To simplify the steps, in order to allow the AWS IAM role to attain service account credential via workload identity we need to do following sequences:
- Create workload identity pool
- Create workload identity pool provider for AWS and set the allowed source AWS account ID
- In workload identity pool provider, do following:
- Create attribute mapping between AWS STS assumed-role credential and google subjects
- Create attribute condition to only allow specific role making the authentication attempt
- Grant access of this workload identity pool to the service account. Select which attribute that will be used as identifier.
- Once it all sets and you have the IAM role credential, you can use the script provided in the materials to generate a service account access token that will be used as google-cloud auth credential
Workload Identity Federation from AWS to GCP Material Resources
You can get a quick overview of the steps above by looking into these resources:
- Terraform Code for Provisioning the GCP service-acccount
- Terraform Code for Provisioning Workload Identity pool and provider
- WorkloadIdentityFederation Implementation
- Script to Impersonate GCP SA from AWS IAM Role
Resources
You can also check the code in this repository. Feel free to change it as you like.